BGP Confederation
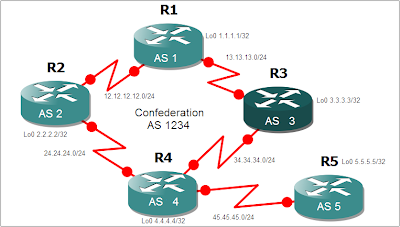
This is feature is used to split an autonomous system into smaller autonomous systems or the reverse which is to combine several autonomous systems into one. Reasons of splitting might be IGP's like OSPF might not be able to handle the routes of a really big enterprise so splitting the AS into smaller will help OSPF scale better, or perhaps the enterprise wants to have separate administrative control per region and wants to control the routing policies on their specific regions. This could also be used if there are company mergers and they want to appear as one AS to other EBGP peers. One thing that intrigues me though is that one of the materials I was using mentioned that this could also be a work around for the BGP Split Horizon Rule. I really doubt that Confederations can be a work around for that. I'll find out for sure in this lab. The diagram below shows 5 Routers with each its own AS number. The goal here to group these routers into one confederation and make them app